This tutorial will show you step-by-step instructions to set up your own speed optimized Shadowsocks (SS) or ShadowsocksR (SSR) server on a Ubuntu VPS. This guide includes installation of the bbr add-on for increased speed on high latency networks and how to use the clients for Windows, Mac, iOS, and Android.
Disclaimer
Shadowsocks is not a VPN.
Creating your own Shadowsocks proxy server can offer good speeds in China, but it lacks some important features compared to using a VPN in China.
- Privacy and anonymity. When you create your own proxy or VPN server, you will be using a static IP address that is tied to your identity. This means that anything you do online while connected to your server can be traced back to you. Make sure you don’t do anything illegal using your server. For example, if you use your own server to download torrents, the hosting provider will likely ban your account if they get a DCMA complaint. The advantage of using a good commercial VPN service is that your anonymity is protected by using shared IP addresses that are not tied to the identify of any individual user.
- Limited support. A VPN works on the network level, which means that all of your traffic is tunneled over the VPN. However, proxies like Shadowsocks work on the browser/application level. That means it will only work for web browsers and applications that specifically support proxy settings. Even in web browsers, proxies don’t work for all types of traffic (Adobe Flash, for example, will bypass all proxies and use your ISP connection directly).
If you want to combine the fast speed of a Shadowsocks proxy and the full privacy of a VPN, the best solution to tunnel a VPN connection over your shadowsocks proxy.
Latest updates for using Shadowsocks in China
November 29, 2019 Update – Black Friday Deals
The 2 Shadowsocks providers that I strongly recommend as an alternative to making your own server are both having very good Black Friday sales right now.
WannaFlix (Shadowsocks and V2Ray)
Black Friday Deal – 1 year for $47
Expires – December 2, 2019
Money Back Guarantee – 30 Days
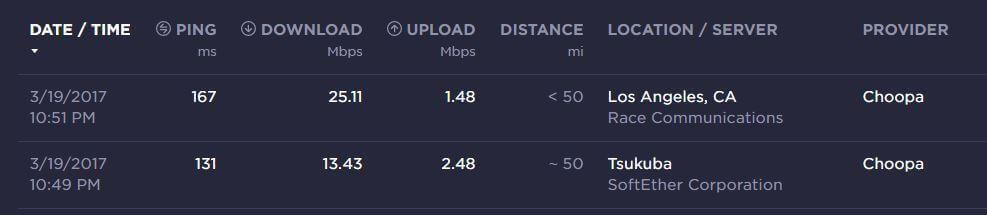
Here are some speed tests for WannaFlix done today from my China Telecom 100/20M WiFi.
WannaFlix Hong Kong PCCW (Shadowsocks)
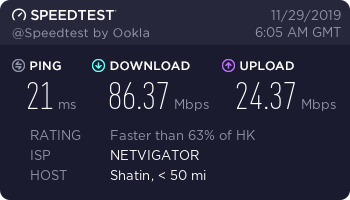
This is a great server with low ping, and it also works for the Hong Kong version of Netflix.
WannaFlix Singapore 4 (V2Ray)
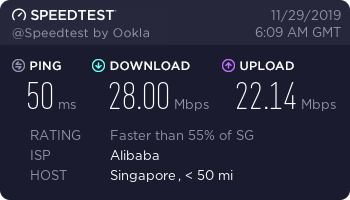
This is also a great server, even though the speed is capped at 30Mbps. It’s hosted on Aliyun Singapore, one of the best CN2 server locations for connections from China. Very high stability and low packet loss. Great for gaming or important video/VoIP calls.
Get the WannaFlix Black Friday Deal
If you miss out on this deal, you can still get 30% off any time with the Tips for China coupon code.
Surfshark (Shadowsocks and VPN)
Black Friday Deal – 2 years + 3 months (27 months total) for $47
Expires – Unknown, but likely around December 15, 2019
Money Back Guarantee – 30 Days
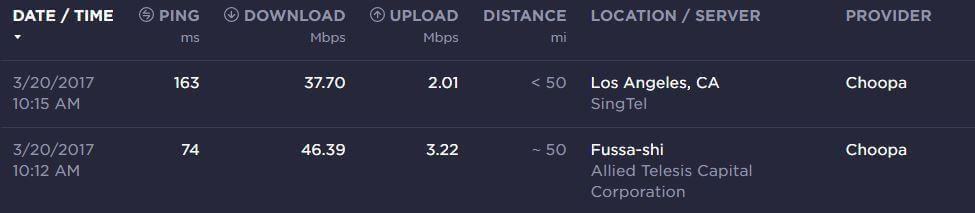
Here are some speed tests for Surfshark done today from my China Telecom 100/20M WiFi.
Surfshark Taiwan (Shadowsocks)
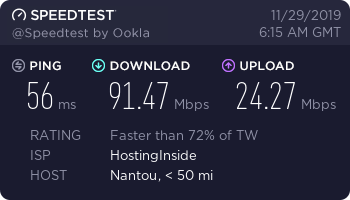
This is my personal favorite Shadowsocks server to use. This server is very fast, and you can watch USA Netflix with it. Surfshark supports Netflix in at least 10 different regions, and the regions that are not supported (such as Taiwan) get USA Netflix.
Surfshark Japan (Shadowsocks)
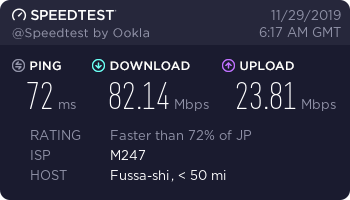
Surfshark can be a little difficult to set up as you need to manually find the good IP addresses for Shadowsocks connections. But I wrote an easy guide here to help you do it.
Get the Surfshark Black Friday deal
If you miss out on this deal, you can still get 2 years for $60 using the links on Tips for China. You just won’t get the additional 3 months free.
October 28, 2019 Update
The Surfshark manual Shadowsocks connections for the Taiwan and Japan servers are still working great. Check my latest guide on how to set up Surfshark manual Shadowsocks connections if you are looking for a good alternative to setting up and managing your own Shadowsocks server.
A Tips for China visitor recently did some speed tests from his Beijing China Unicom 500/100M internet connection for me. The results are very impressive!
Surfshark Taiwan Shadowsocks
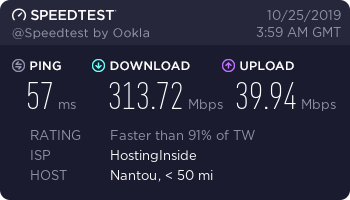
Surfshark Japan Shadowsocks
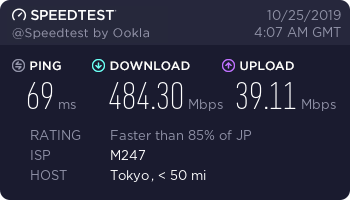
You can see many more recent Shadowsocks test results on the 2020 VPN in China blog page. My internet connection is only 100/20M, so the speeds aren’t as exciting. But I can still come very close to saturating my 100Mbps line.
With the 2 year special and a 30 day money back guarantee, there is really no reason not to try it.
October 12, 2019 Update
Shadowsocks servers were getting blocked more easily recently during the Cyber Security Conference in late September and the National Week holiday during the beginning of October.
During this time, WannaFlix developed a new protocol called Eclipse when all of their Shadowsocks servers were blocked. The Eclipse protocol cannot be blocked by the Great Firewall, so it can always be used as a backup.
Things seem to be back to normal now. WannaFlix Shadowsocks servers are back online and working quite well.
Another new recommendation for a paid Shadowsocks service is Surfshark VPN. They recently added support for manual Shadowsocks connections.
Surfshark is currently offering a 2 year plan for only $60 which is an incredible value (only $2 per month). The Shadowsocks setup is a little bit difficult because you need to find the specific server IPs to enter. Check my latest updates on the 2019 China VPN blog page for some suggested IPs and recent speed tests. The Taiwan and Japan servers are working very well right now.
If you are making your own server on Vultr and find that you can’t get an un-blocked IP address in the US, try some European locations. Those ones don’t get blocked as easily.
May 2019 Update
The ShadowsocksR Windows app was recently updated. There appears to be issues when loading Facebook and Instagram using the latest version 4.9.2.
I recommend using version 4.9.0, which doesn’t have this problem.
Alternatively, you can try setting the DNS server to 8.8.8.8 in the Global Settings of version 4.9.2. This seems to have solved the problem for me, although I have not tested it long enough to be certain that the problem won’t re-appear.
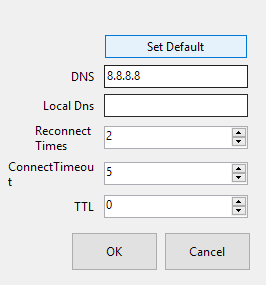
You may need to flush your DNS cache after doing this. To flush your DNS cache, open a command prompt and run the command “ipconfig /flushdns”.
In other news, the WannaFlix Shadowsocks service is still working extremely well for me. Especially the Hong Kong and Taiwan servers.
I highly recommend trying WannaFlix if you have not already.
March 2019 Update
Here are some more speed tests results for the WannaFlix ShadowsocksR service. The tests I did in February were done using an older computer that can only get around 75Mbps on WiFi.
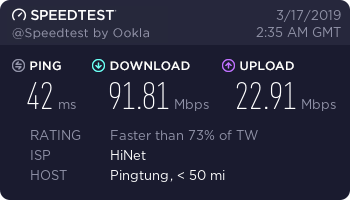
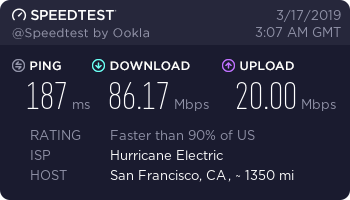
These tests were done on March 17, 2019 using my China Telecom 100/20M connection from a computer that can get closer to the full 100Mbps speed of my line.
Hong Kong Server (PCCW network)
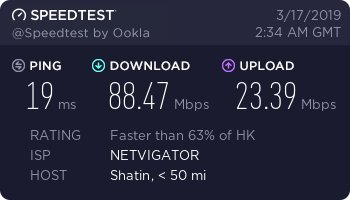
Taiwan Server (Hi-Net network, new)
US Netflix 4 Server (Netflix, Hulu, Amazon Prime, etc)
There are many more servers, including Netflix servers for several regions and a few torrenting servers. Give it a try yourself, totally risk-free with the 30 day money back guarantee. Don’t forget to use the Tips for China coupon code for 30% off.
February 2019 Update
WannaFlix ShadowsocksR service
I recently discovered a good alternative to making your own Shadowsocks server. There is a paid service called WannaFlix, which offers very fast and affordable ShadowsocksR servers.
Although WannaFlix advertises itself as a VPN, it is actually a pure Shadowsocks service. Despite this false advertising, I have to give it a high recommendation due to the high performance servers and low cost.
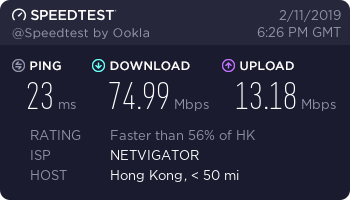
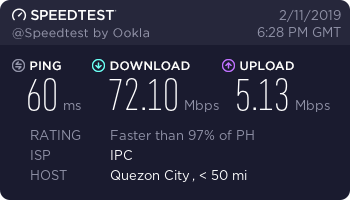
Here are some speed test results using a few of the WannaFlix ShadowsocksR servers, tested on February 11, 2019 from my China Telecom 100/20 Mbps internet connection.
Hong Kong Server (PCCW network)
Philippines Server
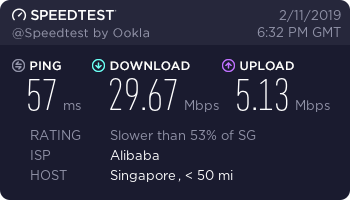
Singapore Server (Aliyun network)
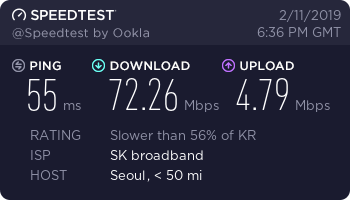
South Korea Server
WannaFlix is currently offering a 30% off coupon code for Tips for China visitors (valid for the first billing cycle only).
Using the coupon code, the price for 1 year comes down to only $58.72 (works out to less than $5/month).
That is an incredible value considering that these servers are hosted on top quality hosting providers. In fact, you would need to literally spend hundreds of dollars per month if you wanted to set up your own servers on these providers.
Not only does WannaFlix have fast servers for China, some of their servers can also unblock Netflix as well. Actually, quite a few of them including USA, UK, Canada, South Korea, Japan, and a few others.
Some of their servers allow torrenting too!
Still not sure if WannaFlix is worth trying? Don’t worry, they are offering a very generous 30 day money back guarantee so you can try it completely risk-free!
Give it a try and compare the performance to your own Shadowsocks server. You will definitely see the value.
Go to WannaFlix now and save 30% with the Tips for China coupon code!
October 2018 Update
The following changes were made to this tutorial on October 13, 2018.
1. Now recommending Ubuntu 18.04 instead of Unbuntu 14.04. It appears that Google BBR now comes pre-installed with the Ubuntu 18.04 Vultr image, so it makes the process much easier. I will leave the BBR installation instructions here in case other providers don’t offer BBR pre-installed on their images.
2. No longer recommending Vultr Tokyo location for China Telecom. The latency has become too high. The best locations for China Telecom these days are the US west coast ones (Los Angeles, Silicon Valley, etc).
3. Now recommending Vultr’s new $3.50/month plan after IPv4 IP addresses were removed from the $2.50 plan.
Some of the images in this tutorial are from before the above changes were made.
Choosing a VPS provider to host your server
Why I am using Vultr for this tutorial
With servers starting from $0.005 per hour ($3.50/month) and good routing to China Telecom, Vultr offers a good combination of price and speed. It’s not the fastest server you can buy, but it does offer the best value for money in my opinion.
Vultr servers are always billed hourly. This is a very useful feature for 2 reasons.
1. If you mess something up and want to start over again, just destroy the VPS and make a new one. It will only cost you $0.01 if you destroy the VPS within the first 2 hours. This is a great way for beginners to learn to use Linux.
2. If your server gets blocked, you can just destroy it and make a new one. You won’t lose money because you only pay for the amount of hours you use the server for.
Once you have used the server for 625 hours (~26 days), then you will pay the monthly price. If you destroy your server before 625 hours, then you will pay for the number of hours that you used. You will see both the monthly and hourly price when you choose your instance. This is not an option to choose, it is just showing you both prices.
Vultr offers a very generous bandwidth allowance that you will likely never go over. The smallest package for $3.50/month includes 500GB of data. The next package for $5/month includes 1TB of data. Note that the data allowance is pro-rated for the amount of hours if you use the server for less than 1 month.
Tip – If you go over this allowance, it’s cheaper to shut down your instance and start a new one rather than paying the excess data fee (or upgrade to a higher price instance).
Vultr Alternatives
If this is your first time setting up a Shadowsocks server, then just stick with Vultr for now and follow this tutorial exactly to the letter.
After you learn the process of making a server using Vultr or if you are already familiar with Linux, you may want to consider some other providers for higher performance (if you are willing to spend more and take the risk of paying monthly/annually instead of hourly).
If you want to try other providers, make sure you choose Ubuntu 18.04 64 bit as the OS and KVM as the virtualization (if available).
Previously this tutorial did not work for OpenVZ virtualization because it is not possible to change the kernel to install BBR. However, now that BBR comes pre-installed on Ubuntu 18.04, this tutorial might work with Ubuntu 18.04 on OpenVZ virtualization (not sure, someone please confirm in the comments if you have tried it).
#1 Alternative – Rackspace Hong Kong
Rackspace Hong Kong has the best network for connections to mainland China. Direct peering to China Telecom (CN2), China Unicom, and China Mobile.
The only problem with Rackspace is that it’s very expensive (over USD $50/month plus USD $0.20/GB).
If the cost is not a concern for you, I would be very interested to know how a shadowsocks server performs on Rackspace. If anyone has tried a cloud server on Rackspace Hong Kong, please let me know about it in the comments below.
#2 Alternative – ExpressVPN Hong Kong 3
The #2 alternative not actually a VPS provider, but rather a VPN company that hosting one of their servers on Rackspace Hong Kong. This is a much cheaper way to get access to a high performance Rackspace Hong Kong server.
The ExpressVPN Hong Kong 3 server is hosted on Rackspace!
Just sign up for ExpressVPN and connect to the Hong Kong 3 server.
Using the ExpressVPN links on this page will give you access to a special offer for an additional 3 months free when you purchase a 12 month subscription. You will get 15 months for the price of 12 months.
If you consider the cost of setting up your own premium China Telecom CN2 server in Hong Kong, paying $99 for 15 months of ExpressVPN is actually very cheap!
The Hong Kong 3 server is hidden away under the “All” section of the app. You won’t find it in the “Recommended” section.
Hong Kong 3 was blocked in November/December last year, but it seems to be back and working better than ever! I have tested the speed of this server at various times over a 24 hour period on Feb 25-26, 2018. You can see the results below.
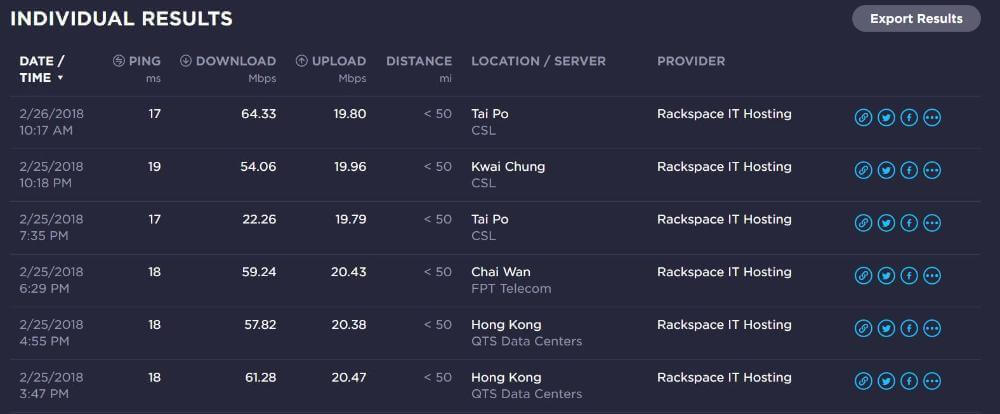
This server has ultra low latency (direct connection to China Telecom on premium CN2 network). Note the very low ping times of only 17-19 ms. The download speed is not too bad either!
I’m also running this server on a cheap 180 yuan router from Taobao that I use for video streaming. Check out my tutorial on this router here. This router can get around 20Mbps download speed on Hong Kong 3.
Here is the best part.
Every ExpressVPN subscription comes with a no-hassle 30 day money back guarantee. Get a full refund any time within 30 days. No sneaky terms and conditions. Just ask for a refund if you are not satisfied and you will get one!
In case the Hong Kong 3 server gets blocked again or is unavailable, the Hong Kong 5, Hong Kong 4, Taiwan 1, and Taiwan 2 servers also have premium routing to mainland China ISPs.
#3 Alternative – Bandwagon Host
I have not tried this one yet, but several people have suggested it. They offer China Telecom CN2 servers hosted in Los Angeles.
USA CN2 servers are not as fast as Asian CN2, but it should be faster than Vultr and other providers.
The special China Telecom CN2 servers are only offered though this page. The servers offered from the regular homepage are not the CN2 ones.
After using the above link, find the special called SPECIAL 10G KVM PROMO V3 – LOS ANGELES – CN2.
When you check out, make sure the location is US – Los Angeles DC3 CN2 (USCA_3). There is another promo package for $19.99 per year, but this is not the CN2 location.
I heard rumors that Bandwagon Host does support a limited number of IP address changes if your server gets blocked. I have sent a request asking for details about this and I will update here when I get the official answer about this.
Update: Here is the answer from Bandwagon Host regarding the IP address changing policy.
James: What is your policy for changing IP addresses if the IP gets blocked by China GFW? Your TOS mentions something about a fee for changing IP but doesn’t say how much the fee is.
Bandwagon Host: We change this policy and fees from time to time. We guide customers through the process of changing IP when the need arises (be it free replacement or not). Usually the fee to replace IP is between $2 and $20.
James: What is the current policy right now? Between $2 to $20 is a very big range. Can you provide more information about this?
Bandwagon Host: I am very sorry, but we are not able to provide any more assistance on these questions.
It seems they don’t want to answer my questions about this.
If anyone has first-hand experience on this issue, please leave a comment.
Unlike Vultr and Rackspace, I believe Bandwagon Host counts the data allowance as INPUT + OUTPUT. With a proxy server, the data input and output is approximately be the same. This means that 500GB from Bandwagon Host is is actually only 250GB of traffic.
Vultr, Rackspace, and Aliyun only count OUTPUT data so you get the full amount of data that they advertise.
#4 Alternative – Aliyun Hong Kong
Alibaba Cloud (aka Aliyun) does offer Hong Kong CN2 servers at a better price than Rackspace, but there are some drawbacks.
I’m going to move the Aliyun information to a new page because Aliyun is very complicated and this page is already long enough.
Check this page for more info about Aliyun.
#5 Alternative – Other Providers
I don’t know much about these ones except that they are popular choices for Shadowsocks users in China. I will just leave the links here and you can do your own research. Be sure to leave a comment if you have tried any of these.
Kdatacenter – Premium South Korea VPS (recommended if you are near Shanghai)
Gigsgigscloud – Variety of different Hong Kong and USA servers
Choose the best server locations for your ISP
Before we get started, it’s a good idea to do some network analysis to find the best Vultr server location for your Shadowsocks server.
Using the hostnames below, send a ping command to each server to check the latency to your location. Remember to turn off any existing VPN connections, because we want to check the latency between your ISP and the Vultr servers.
The locations shown in bold have the best routing to China Telecom.
| Tokyo, Japan | hnd-jp-ping.vultr.com |
| Singapore | sgp-ping.vultr.com |
| Silicon Valley, California | sjo-ca-us-ping.vultr.com |
| Los Angeles, California | lax-ca-us-ping.vultr.com |
| Seattle, Washington | wa-us-ping.vultr.com |
| Frankfurt, DE | fra-de-ping.vultr.com |
| Amsterdam, NL | ams-nl-ping.vultr.com |
| Paris, France | par-fr-ping.vultr.com |
| London, UK | lon-gb-ping.vultr.com |
| New York (NJ) | nj-us-ping.vultr.com |
| Chicago, Illinois | il-us-ping.vultr.com |
| Atlanta, Georgia | ga-us-ping.vultr.com |
| Miami, Florida | fl-us-ping.vultr.com |
| Dallas, Texas | tx-us-ping.vultr.com |
| Sydney, Australia | syd-au-ping.vultr.com |
If you are using Windows, you can download my Vultr ping script to automatically ping all of Vultr servers.
I have identified 4 servers that have a decent ping time to my China Telecom connection.
- Tokyo
- Singapore
- Silicon Valley
- Los Angeles
I am going try a Tokyo server and a Los Angeles server.
To avoid confusion, I will just show the instructions for setting up 1 of the servers, although I am actually doing both at the same time.
2019 Update – Tokyo is no longer a recommended location due to degraded performance since this tutorial was first made. I now recommend US west coast locations. Or you can try Europe locations if you can’t find an unblocked IP in the US.
Deploy your instance
The first step is to go to Vultr and create an account if you don’t already have one. You will need to fund your account with a minimum $5 deposit using PayPal or verify a valid credit card.
When I first signed up, I used my Chinese credit card and I was asked to verify my identity by sending them a copy of my passport and the credit card I used. I suspect that they asked for this because I was connected to a VPN when I added my credit card and the IP address did not match the country of my credit card.
I recommend turning off your VPN if you are using a Chinese credit card or Chinese PayPal account to avoid this fraud detection. If you are are using an overseas credit card, you may want to connect to a VPN in the same country as your credit card, or turn your VPN off. I’m not sure which option is better in this case.
Although Vultr offers WeChat payments, this won’t work for you unless you have a Chinese ID card (only Chinese citizens can use WeChat and Alipay for merchants outside of China).
Once your account is funded/verified then you can deploy a new instance (VPS).
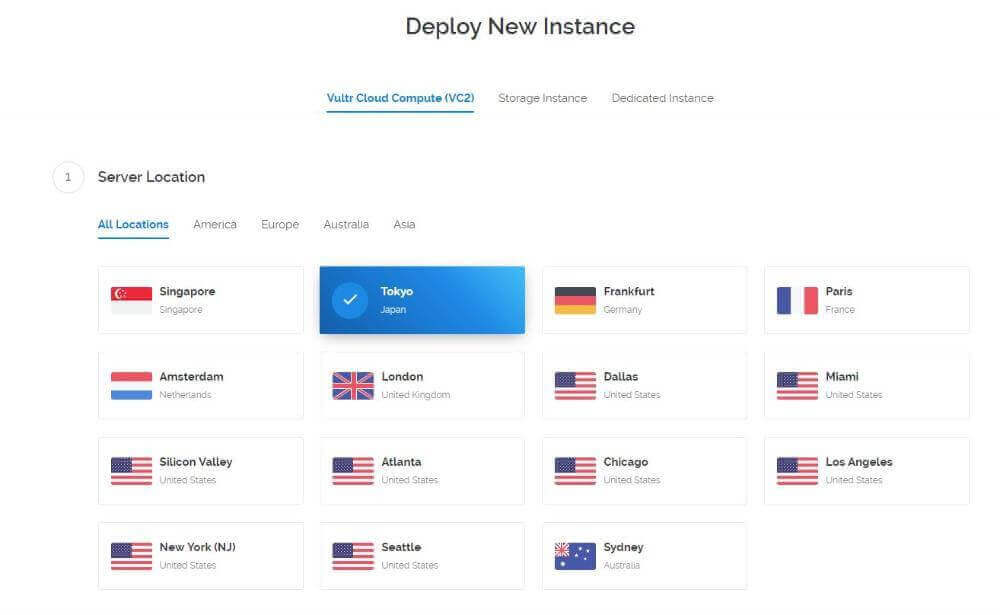
Choose your location.
Choose the server type (OS). For this tutorial, I am using Ubuntu 18.04 x64.
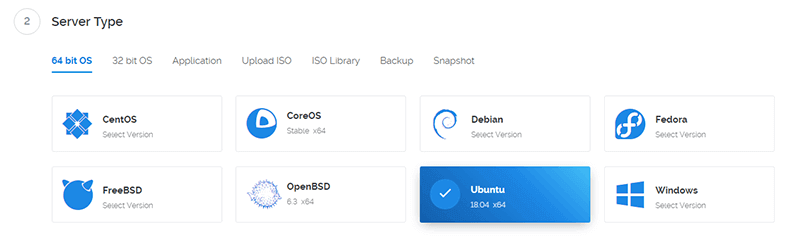
Choose the server size, the $3.50/month ($0.005/hr) with 20GB, 512MB memory, and 500GB data, is all you need for a personal shadowsocks server.
Choosing a more expensive instance will not increase the performance of your server. The only reason to choose more expensive instance is if you need more than 500GB of data per month.
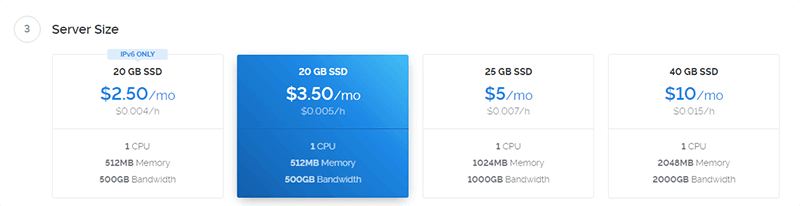
Note: As of October 2019, the only location with $3.50 instances available is New Jersey. If you don’t want a server in New Jersey, you will have to pay $5.
Leave everything else as default until section 7, do not enable IPv6 (untick it if it’s selected).
Now enter a hostname, you can put anything. I entered tokyo.com for my hostname. As we are not using our VPS to host a website, it doesn’t matter what you put here. You can also leave it blank with Vultr but some other VPS providers will require you to enter something here.
Press Deploy Now to deploy the VPS.
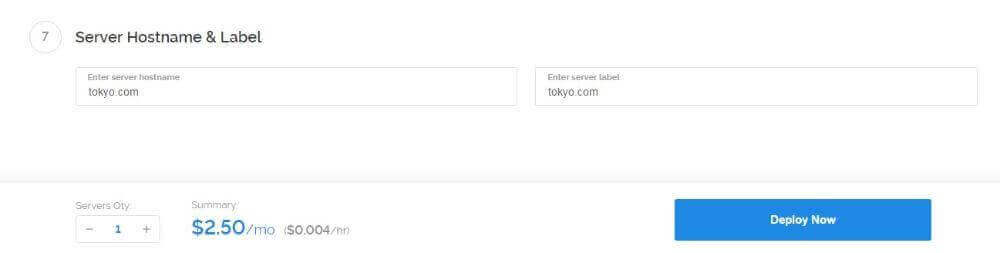
Wait until your VPS is finished installing and the status changes to “Running”. Then, click on the server to open the server details.

We will need the IP address and password to log into our server by SSH.
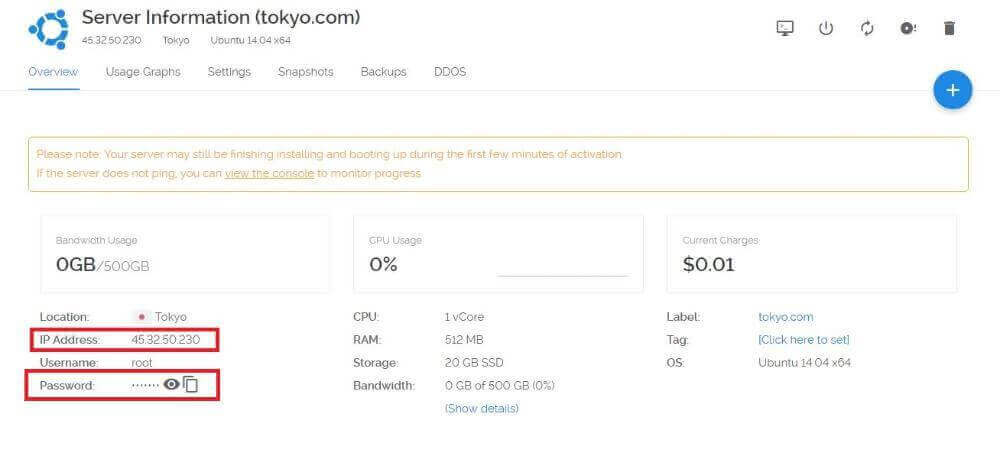
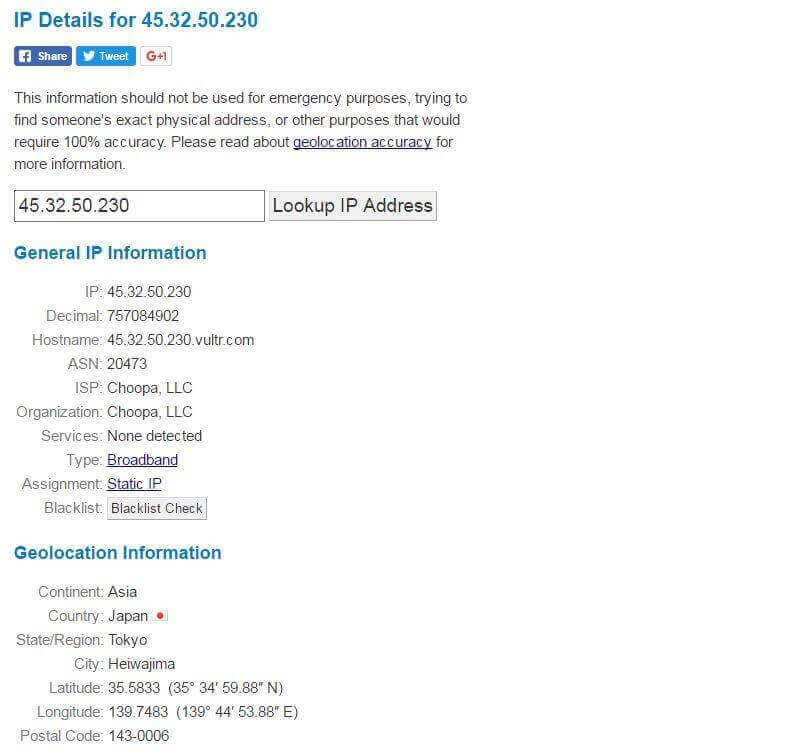
The first thing I do after deploying a new VPS is look up the IP address in a geo-location database to see if it shows the correct location. Many Vultr Asian servers are incorrectly geo-located in the USA. If the IP address is not showing the correct location, then I will just destroy the instance and deploy a new one (remember, it only costs $0.01 if you destroy an instance within the first few hours).
Using a shadowsocks server with an IP address with the wrong geo-location can be annoying. You will need to manually choose the correct server when doing a speed test, Google will think you are in the wrong country, etc.
After looking up the IP address, I can see that it is correctly listed as Tokyo.
Ok, time to connect to our server using SSH.
If you are using Mac, you can use the Terminal program to start an SSH session with your server.
Open Terminal and enter the following command (Mac users only):
ssh server_ip -p 22 -l root
replace server_ip with the IP address of your server.
For example, using my server in this tutorial, you would enter the following.
ssh 45.32.50.230 -p 22 -l root
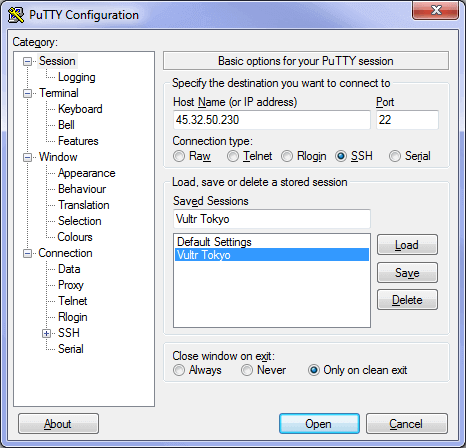
Unlike Mac, Windows does not come with an SSH client.
I am using Windows, so I have downloaded Putty.
If you are using Putty for Windows, enter the IP address of your Vultr server and press open to connect to it. Leave all of the settings as default. You can save the session so you don’t need to enter the IP address next time, I saved the settings as “Vultr Tokyo”.
Accept the security warning and then login as root and enter the password from the Vultr server management page.
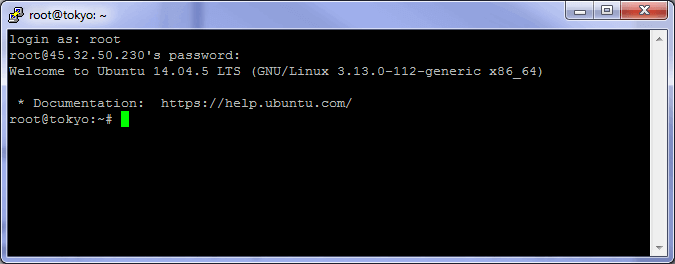
Tip – To paste text from the clipboard using Putty, simply press the right mouse button once and whatever is in the clipboard will get pasted. When typing or pasting your password, you won’t see anything on the screen. Just press enter after you have typed it or pasted it by single clicking the right mouse button.
If your SSH connection is not successful, wait a few more minutes and try again. When you first create a server, it can take up to 5 minutes until it’s ready to use.
If you still can’t connect after your server is ready, that means your IP address is blocked by the Great Firewall of China (probably due to the person who used that IP address before you).
This can be confirmed by connecting to a VPN to see if you can connect.
If your IP is blocked, then destroy your instance and make a new one.
Once you have a good IP address that is not blocked and you are logged in successfully, your screen should look like this.
Install ShadowsocksR
Update and upgrade the machine by entering the command below.
sudo apt-get update && sudo apt-get upgrade -y
Any time that you see highlighted text like the text in the above line, enter it as a command. I will only show the screenshot for the first command, shown below.
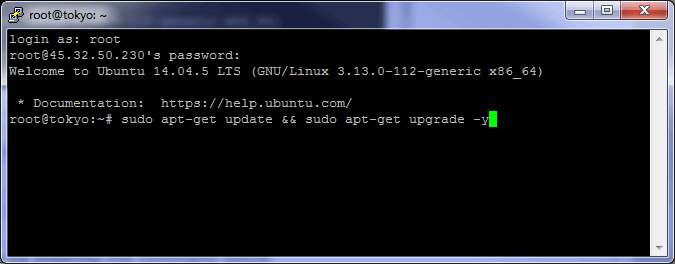
After you enter the command, press enter to execute it.
When executing this first commend, you may get a message that says something like this:
“A new version of configuration file /etc/default/grub is available, but the version installed currently has been locally modified. What do you want to do about modified configuration file grub?”
You can just press enter to keep the default option of using the current one.
Now, let’s install shadowsocks on the server. There are many different versions of shadowsocks and many different ways to install them. I am going to install ShadowsocksR (SSR) using an installation script from GitHub user teddysun.
Teddysun has made some great scripts that make it very easy to install different versions of shadowsocks and other linux applications.
There used to be a donation page (https://teddysun.com/donate) where you could send a donation to Teddy Sun by WeChat or Alipay to support his good work. However, that link is now dead and I can’t find any similar page on his website now. If anyone knows how to support the work of Teddy Sun, please let me know what link I can include here.
Enter the following 3 commands to download the run the SSR installation script.
wget – no-check-certificate https://raw.githubusercontent.com/teddysun/shadowsocks_install/master/shadowsocksR.sh
Note – The above command is shown on 2 lines because it’s too long. Make sure you copy the full command starting with wget and ending with shadowsocksR.sh
chmod +x shadowsocksR.sh
./shadowsocksR.sh 2>&1 | tee shadowsocksR.log
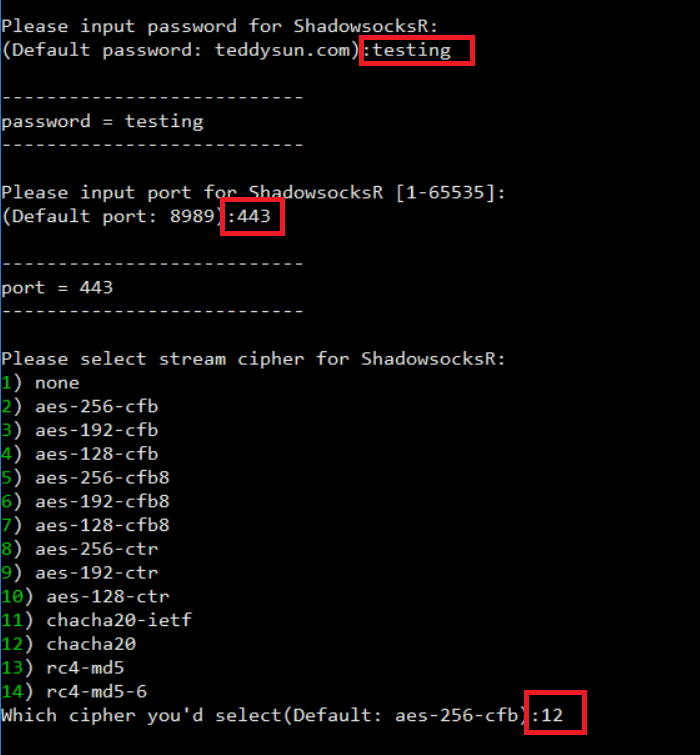
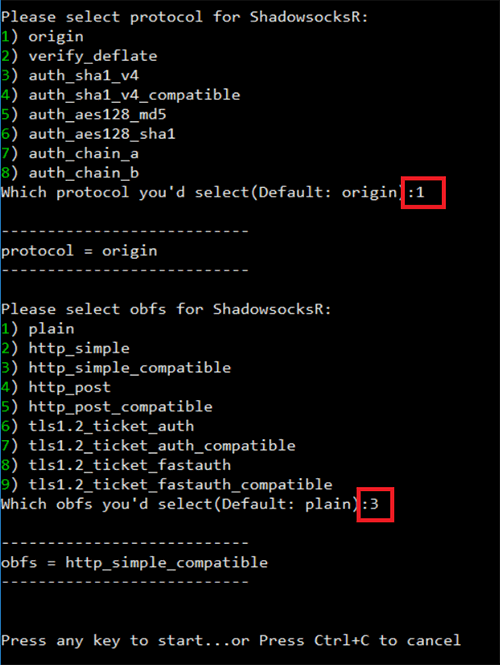
Enter the parameters that you want to use for your server. Here is what I am using for this tutorial. You can always change these settings later if you want so don’t think about it too much.
Password: testing
Port: 443
cipher: chacha20
protocol: origin
obfs: http_simple_compatible
After you enter all of the settings, press any key to start the installation. It will take about 5 minutes.
February 2019 Update – Try protocol auth_sha1_v4_compatible instead of origin.
If you want to make any changes to the configuration, enter the command below to edit the server config file.
nano /etc/shadowsocks.json
Press Ctrl + X to exit. When asked to save the modified buffer, press the y key once and then press enter to keep the same file name.
Every time you make changes to this file, you need to restart shadowsocks so the changes will take effect. Restart shadowsocks using the command below (if you have changed the config file).
/etc/init.d/shadowsocks restart
The server is already running, you can download a shadowsocks client and try it now.
Download a client and test your server
The standard Shadowsocks (SS) client is no longer stable in China. I recommend using the ShadowsocksR (SSR) client if you are in China.
SSR Clients (recommended for China)
ShadowsocksR for Windows (Download version 4.9.0, the newer ones have DNS leaks)
iOS Potatso Lite (FREE)
iOS Shadowrocket ($2.99)
Original SS Clients (NOT recommended for China)
Note for iOS Users
For iOS, I highly recommend paying $2.99 for Shadowrocket because WhatsApp calls and other VoIP applications don’t work with Potatso Lite or any other iOS app. Shadowrocket is the only stable Shadowsocks client for iOS that will tunnel VoIP through the proxy, so it’s definitely worth the price for it.
Apple has removed all VPN and Shadowsocks apps from the China version of the app store. If your iTunes account is registered with a Chinese address, you need to create a new iTunes account with a foreign address to download these apps.
If you are using a USA iTunes account but don’t have a US credit card to buy apps, you can always buy a $5 USA iTunes gift card on Taobao.
Shadowsocks vs ShadowsocksR (SSR)
The original version is called Shadowsocks (SS). ShadowsocksR (SSR) is a newer version that supports obfuscation, which can make your shadowsocks traffic look more like regular https web traffic. This can prevent your speed from getting throttled by your network or ISP.
The server that we just made is compatible with both SS and SSR clients (if you chose the same parameters as me when creating your server).
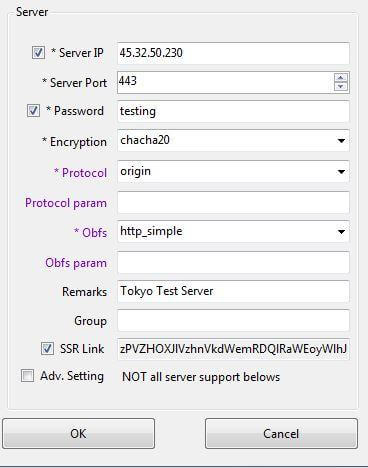
All of the clients are a little bit different, but basically you need to enter the following settings (assuming you chose the same options as me).
Server – The IP address of your server
Port – 443
Password – testing (or whatever password you chose)
Encryption – chacha20
Protocol – origin or auth_sha1_v4 (if you choose auth_sha1_v4_compatible for your server, this option is only available for SSR clients)
Obfs – http_simple for obfuscation or plain for no obfuscation (this option is only available in SSR clients)
If there are any other options, leave them as default. Do not enable onetime authentication.
You need to be careful with these settings. If you don’t get it exactly right, then it will seem like the proxy is connected, but you won’t have any connection to the internet. Unlike a VPN, you cannot easily tell if the proxy is actually connected successfully or not.
Here are my settings using the SSR Windows client.
The way that you enable the system proxy will depend on the version of the client you are using.
Using the SSR Windows client:
Enable the proxy by choosing Mode –> Global or Mode –> PAC.
Disable the proxy by choosing Mode –> disable system proxy.
TIP – Make sure you remember to disable the system proxy before you exit the client or shut down your computer. Otherwise, you will find that you have no internet at all. To solve this problem, just open the shadowsocks client and disable the system proxy.
Global vs PAC Mode
Global will route all domains through the proxy, while PAC will only use the proxy for a specific list of blocked websites such as Google, Facebook, etc and use your ISP connection for everything else. Not every blocked website is part of this PAC list. And even foreign websites that are not blocked are very slow if not using a proxy or VPN.
For this reason, I recommend using the Global mode. It’s easy enough to enable/disable that you can conveniently switch it off if you need to access some Chinese websites.
You can also can choose the “Bypass LAN & China” proxy rule to automatically bypass the proxy when connecting to websites or servers in China. This will only bypass the proxy for known China IP addresses and use the proxy for everything else (assuming you are in Global Mode).
Once you have enabled the system proxy using the client, most browsers and applications should work by default. Chrome and IE, for example, will use the system proxy settings (unless you have an extension installed that is controlling the proxy settings).
Other browsers or programs, such as Firefox, may need to be set manually to use the system proxy or use a SOCKS5 proxy on server 127.0.0.1 port 1080 (port 1086 for Mac). The proxy settings can usually be found in the advanced settings for most applications.
Proxies will not work for all programs and all types of web traffic. Sometimes you need to use a VPN for certain things. It is also possible to tunnel a VPN connection over shadowsocks for better VPN performance.
Let’s check the performance of my Tokyo and Los Angeles servers.
Both servers are working but the speed is not great.
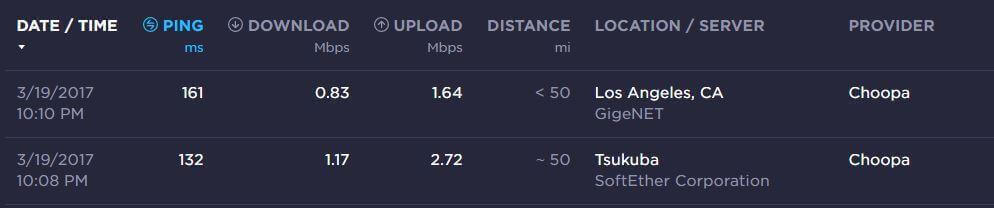
When testing the speed of shadowsocks, you must remember use an html5 speed test such as beta.speedtest.net because all proxies will bypass Adobe Flash and you will only test your connection without the proxy if you use speedtest.net or other Flash based speed tests.
Install Google BBR and Optimize the Server
Google BBR is a TCP congestion control algorithm that can give a huge speed boost on networks with high packet loss (basically all of the networks in/out of China).
October 2018 Update – As Google BBR is now included by default with Ubuntu 18.04 on Vultr, you can skip this step. You will still need to do this if you are using a different version of Ubuntu or if using another VPS that doesn’t include BBR with their Ubuntu 18.04 image.
To confirm whether Google BBR is already installed, enter the following command.
lsmod | grep bbr
If you see a text output from this command with the words “tcp_bbr” and a number beside it, then you already have BBR. You can skip the next command.
If you are using an older version of Ubuntu or don’t have BBR installed, then install it using the command below (another great script from Teddy Sun).
wget – no-check-certificate https://github.com/teddysun/across/raw/master/bbr.sh && chmod +x bbr.sh && ./bbr.sh
If you have an incompatible kernel, you will be asked to reboot your server after the kernel is changed. You will need to re-connect using Putty after rebooting.
You can confirm that the installation was successful by using the “lsmod | grep bbr” command again.
Now that bbr is installed, we just have a few more settings to optimize.
Next, change the kernel configuration settings.
nano /etc/sysctl.conf
Add the following lines at the bottom of the file after the net.ipv4.tcp_congestion_control = bbr line.
fs.file-max = 51200
net.core.rmem_max = 67108864
net.core.wmem_max = 67108864
net.core.netdev_max_backlog = 250000
net.core.somaxconn = 4096
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_tw_reuse = 1
net.ipv4.tcp_tw_recycle = 0
net.ipv4.tcp_fin_timeout = 30
net.ipv4.tcp_keepalive_time = 1200
net.ipv4.ip_local_port_range = 10000 65000
net.ipv4.tcp_max_syn_backlog = 8192
net.ipv4.tcp_max_tw_buckets = 5000
net.ipv4.tcp_fastopen = 3
net.ipv4.tcp_mem = 25600 51200 102400
net.ipv4.tcp_rmem = 4096 87380 67108864
net.ipv4.tcp_wmem = 4096 65536 67108864
net.ipv4.tcp_mtu_probing = 1
Press Ctrl + X to exit and then press Y to save the file, and press enter to keep the same file name.
Apply the new settings by entering the command below.
sysctl -p
Let’s make a few more optimizations.
nano /etc/security/limits.conf
Add these lines to the bottom of the file, include the * symbol.
* soft nofile 51200
* hard nofile 51200
Press Ctrl + X to exit and then press Y to save the file, and press enter to keep the same file name.
Next, enter this command.
nano /etc/pam.d/common-session
Add the following line at the end of the file.
session required pam_limits.so
Press Ctrl + X to exit and then press Y to save the file, and press enter to keep the same file name.
nano /etc/profile
Add the following line at the end of the file.
ulimit -n 51200
Finally, type the command below.
ulimit -n 51200
Restart the shadowsocks server again.
/etc/init.d/shadowsocks restart
The optimizations are finished!
I can see a big improvement in the speeds after the optimizations.
The speed is between 10 times and 25 times faster now!
The speed test was done at 11pm, the speed will be even faster during non-peak hours.
Speed test the following morning…
Bonus Section – Advanced Customization
How to open more ports and share your server with friends
Warning! Make sure you only share your server with friends or people who you trust because you will be responsible for any illegal activities originating from the IP address of your server.
The easiest way to share you server is to simply tell your friends the port number and password of your server. Everyone can use port 443 with the same password, there is no limit to how many simultaneous connections can be made.
However, if you want to give each user their own unique port number and password, you can edit the shadowsocks.json file.
nano /etc/shadowsocks.json
Delete all of the contents of the file and then paste the contents below (using your own combination of port numbers and passwords that you wish to use).
{
"server":"0.0.0.0",
"server_ipv6":"::",
"port_password": {
"443": "password1",
"1194": "password2",
"8000": "password3",
"8383": "password4",
"8384": "password5",
"3000": "password6",
"3001": "password7",
"3002": "password8",
"3003": "password9",
"3004": "password10",
"3005": "password11",
"3006": "password12",
"3007": "password13",
"3008": "password14",
"3009": "password15",
"3010": "password16"
},
"local_address":"127.0.0.1",
"local_port":1080,
"timeout":120,
"method":"chacha20",
"protocol":"origin",
"protocol_param":"",
"obfs":"http_simple_compatible",
"obfs_param":"",
"redirect":"",
"dns_ipv6":false,
"fast_open":true,
"workers":1
}The above configuration is just an example, you can use whatever ports and passwords you want.
Don’t forget to restart shadowsocks after you make changes to the config file.
/etc/init.d/shadowsocks restart
How to limit data per user/port
There is probably a much better way to do this, but this is the method I found.
This is a quick and easy way to get this job done but it has a major flaw. If your VPS is rebooted, then the data counters will be cleared. Theoretically, there should be some way to save the byte counters and restore them after a reboot. Or, there is probably is a better way to do it altogether, but I don’t know any such method so I will just show you what I know.
If you know of a better way to do this then get in touch with me by email and let me know your method so I can update this page.
In this example, I will add firewall rules to limit the data transferred on each port. I will add a data limit of 50GB for port 443 and 10GB for each of the other ports I have set up.
Enter the following commands (using the port numbers which you have configured with the data limit in bytes that you want to set).
sudo iptables -I OUTPUT -p tcp – sport 443 -j DROP sudo iptables -I OUTPUT -p tcp – sport 443 -m quota – quota 50000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 1194 -j DROP sudo iptables -I OUTPUT -p tcp – sport 1194 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 8000 -j DROP sudo iptables -I OUTPUT -p tcp – sport 8000 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 8383 -j DROP sudo iptables -I OUTPUT -p tcp – sport 8383 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 8384 -j DROP sudo iptables -I OUTPUT -p tcp – sport 8384 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3000 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3000 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3001 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3001 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3002 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3002 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3003 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3003 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3004 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3004 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3005 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3005 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3006 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3006 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3007 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3007 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3008 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3008 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3009 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3009 -m quota – quota 10000000000 -j ACCEPT sudo iptables -I OUTPUT -p tcp – sport 3010 -j DROP sudo iptables -I OUTPUT -p tcp – sport 3010 -m quota – quota 10000000000 -j ACCEPT
To check the firewall rules and how much data has been used by each user/port, enter this command.
Note – Adjust the width of the Putty or terminal window before entering this command because the default width is not enough to show the output correctly.
sudo iptables -nvL -t filter – line-numbers
Use the scrollbar on the right of the Putty windows to scroll up and see the OUTPUT chain.
In this example, I have added 32 new firewall rules to the top of the OUTPUT chain. The output of the OUTPUT chain of the above command should look like this (2 rules for each port).
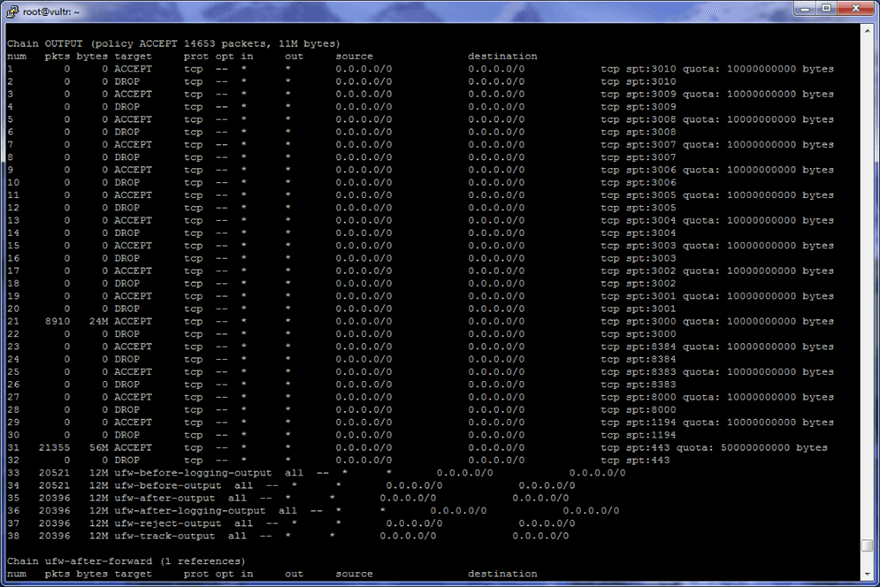
Make note of the first column (chain number) for each line. The chain number will be used in some of the commands below.
As you can see, I have used 24MB of data on port 3000 and 56MB of data on port 443 since adding these firewall rules. Once the quota has been used up (50GB for port 443, 10GB for all other ports in my example) for a specific port, then the proxy will stop working for the user/users of that port (until you reset the counter or reboot the server).
To clear the data counters for all users/ports, enter this command.
sudo iptables -Z OUTPUT
To clear the counter for a specific user, enter this command.
sudo iptables -Z OUTPUT #chain number
#chain number = The number shown first column when you use the “sudo iptables -nvL -t filter –line-numbers” command shown above.
For example, to clear the byte counter for port 443, this is the command.
sudo iptables -Z OUTPUT 31
Now the data counter for port 443 has been reset to 0.
To delete the firewall rules for a specific port, first note the 2 chain numbers related to port you want to delete. For example, to remove the data limit for port 3000, we need to delete chain numbers 21-22.
sudo iptables -D OUTPUT 21
sudo iptables -D OUTPUT 21
Note – The above commands are not a mistake, you enter the same command twice. After you delete chain #21 then all of the chains below it will shift up. Chain #22 becomes chain #21, #23 becomes #22, so on and so fourth.
To make these firewall rules persistent after a reboot, use the following commands.
Note – The data counters will still be reset to zero after a reboot, only the rules themselves will be persistent.
sudo apt-get install iptables-persistent
sudo invoke-rc.d iptables-persistent save
This is the end of the bonus section for now. Maybe it will be updated to include more later on…

Thanks for sharing!
I’ve got a question. I wanna use two vps in order to bypass geo-restrictions:
vps one in Russia and vps two in UK
Now I wanna connect through Russia shadowsocks to UK shadowsocks.
How can I achieve this?
can anyone of you give me codes for login in on SS android in China? I can’t do all that on a pc, so I need someone’s help.
Not sure what “codes” you are referring to.
can we use linux based shadowsocks client to route all traffic of LAN to Server. ?
Hi James/ Author of this post !!!!!!!
1. Can i route VOIP traffic through ShadowSocks/ ShadowSocksR ? If yes then how it is possible ?
Where do you want to use VoIP? On mobile or PC? I also have same requirement with you.
Short version of whats working for me. I started writing a full version but it was too much info. Ask me questions if you need. This hasn’t been blocked for at least a week with good speed.
I thinks this works on AWS Free tier(they charged me a dollar for something though lol. Vultr is easier and cheap too. I like using US servers.
Type this command on your VPS.
bash <(curl -s -L https://git.io/v2ray.sh)
It installs V2ray server and Shadowsocks server(not SSR, Theyre different) its in chinese but its easy.
1.install 2.uninstall
Experiment with settings.
mkcp is fast fast but eventually gets blocked. I use mckp with dtls.
Tcp, HTTP2, Websocket, all seem to work slowly but not get blocked (Good for a backup?)
any port, any password
Install ad blocker? I always choose No
YES to install Shadowsocks.
any port, any password
use aes-256-cfb
you can copy the urls to import settings into client.
For windows client I use SSR client(can connect to SS servers) with global mode and “bypass lan and china” checked
Or also windows, V2rayN which connects to both V2ray and SS servers(not SSR servers) but i cant figure out its PAC mode or bypass china settings or whatever.
on android i use v2rayng it can connect to both SS and V2ray servers(not SSR servers). It has a “per app”
Im fairly certain it helps prevent detection if your china traffic bypasses your server. especially on cellphone.
This was the short version. LOL
Hope it helps. Mines still working. Good luck.
Yes AWS free tier is also good to use. I’m using it now. But the bad news is I have to apply a new AWS free tier every year.
Hello Master or James?
I’m just followed this article setup a SSR over Vultr.com. And used only 10 minutes then down. SSH is still alive to VPS, only the SSR stop work.
Before I found your web, I have used own SS on free AWS for a while. Every time it’s blocked, I change a new IP address. But in the past 2 months, this way doesn’t work any more.
It happen to me like what I wrote above, only live 5 to 10 minutes for every new IP.
Do you have any idea? Thank you very much!
BTW, I also leave message for you on LinkedIn.
wow, I make it works again after changing the combination of protocol and ofs. Here is what I’m using:
“method”:”chacha20-ietf”,
“protocol”:”auth_sha1_v4″,
“protocol_param”:””,
“obfs”:”tls1.2_ticket_auth”,
Anyone got problem, maybe you can try above.
“method”:”chacha20-ietf”,
“protocol”:”auth_sha1_v4″,
“protocol_param”:””,
“obfs”:”tls1.2_ticket_auth”,
Tried that configuration but didn’t work either. SSR dead after a few minutes of use. I have changed the sever_port parameter and it will work again for a while
Where you put your VPS on?
I used Vultr.com on Singapore and already used for 5 days, and still alive.
In the beginning, I used port 443, with simple password as the example in this tourist.
But after I changed to the parameters I post, and setup a more strong password, it looks work well.
Now I’m using port 16000+.
Worked great for about 10 min at a time on each port til my IP got blocked and could no longer putty into server. The console on vultr still worked. Do you think it’s worth doing another one with a new IP or is there a different type of server that might work better like Algo, routeros, or the vultr openvpn? Man Shadowsocks is fast when it works though! Is yours getting blocked really quick? I’m using the correct version of SSR client. I have vultr credit now and I guess I’ll try some things. Lol. This is my first try with cloud computing. It’s pretty great.
Hi Ed,
I’ve also created multiple servers on vultr and set up ShadowsocksR following this guide but all of them got blocked within an hour or two. It’s frustrating because it used to work so well! Playing around with settings, I’ve had luck with “no cipher”, “auth_chain_a”, and “tls1.2_ticket_auth”. My Japan server has been running for 48 hours without any problems so far. Mind you, I’m using Toyo’s script(https://github.com/ToyoDAdoubi/doubi/blob/master/ssrmu.sh), since Teddy Sun has stopped working on his. it’s in Chinese though.
I hope it helps!
right now im having pretty good luck with a v2ray server in LA on Vultr. very similar to setting up a SS server. Seems to be working acceptably fast (only like 1-2 MBps) and so far hasnt been blocked for a couple days.
Thank you very much for this very useful tutorial James! It works perfectly!
Do you know any methods that we could use to limit the number of uses on each port? For example, if I give the port 443 to one user and I set a limit of two devices, he can only use the account on one computer and one phone (or two computers).
Hi guys, is this still working in late December 2019?
can we use linux based shadowsocks client to route all traffic of LAN to Server. ?
Is it possible to make Shadowsocks work for IPv6?
On a computer, (Windows) I am using ShadowsocksR version 4.9.0. On the phone, (Android) is also ShadowsocksR 3.5.4. Mobile Operator China Mobile. All ip addresses are blocked immediately after creation. If someone knows how to solve this problem, please help.
The blocks are usually just temporary. If you put your phone in Airplane Mode for a few seconds then it will work again. You can check the ping.pe website to see if your IP is actually blocked or not.
Thanks for the advice! I will continue testing.
Hey. for some reason occasionally I cant access youtube / google at some points. sometimes a reboot fixes it , sometimes it does not. I can ping my server from my local computer and I can ping said websites from the server. But for some wierd reason it will not ping from me 0o I have no idea what the problem could be. Tried looking for a solution online now for dais but cannot find anything that helps.
I am using the vypr setup.
Thanks for any help and tips.
Are you using Windows or another OS? If Windows then I assume you downloaded the newest version of the client software from the Github page? You should download version 4.9.0 instead. See the May 2019 update near the top of this page for more info.
I will update the download section of this page and include a note there as well.
This issue happens to me as well! Initially I thought it was my server issue, but actually it’s related to the network. I can ssh to my server, but I can’t ping the port.
Hoping to find a solution.
If you are using the Windows client version 4.9.2 then the problem is DNS leaks. Use version 4.9.0 instead.
@James I am using windows shadowsocks 4.9.0. Could it be the iOS shadowrocket app?
If you can connect to your server by SSH but the ping test in Shadowrocket fails, then your port might be blocked. Changed your server port.
Yes, so far I tried to change to a different port and it works. I am just wondering if there’s a long term solution to this without constantly changing port every now and then.
When you mentioned port is blocked, do you mean that GFW blocks the port number? If that’s the case, I am quite surprized that the GFW is able to know the port, because I thought the port number is encrypted as well. Is there a solution to this, maybe close the port to everyone except myself?
No, of course your port number is not encrypted. That’s not how encryption works.
You can set up multiple ports on your server so you can easily switch between them in your client without having to log into your server to change it.
Port blocks are rare, doesn’t happen that often. When it does, it will usually get unblocked again after a few days.
I see. Nowadays, it seems I have trouble pinging my server (it says timed out), but only for a few seconds to a minute. Whenever I tried to watch a video, the video will stop loading for a minute, then will keep playing after that. This happens a lot of times these days.
Is it due to the GFW trying to limit the SSR traffic by blocking the IP? Do you encounter this issue as well? Thanks.
Yes, same problem here, started on Wednesday night. GFW is now targeting SS/SSR traffic with temporary blocks. VPN connections seem to be working better than Shadowsocks right now.
It seems that the combination of a Windows based Internet browser and a Windows SSR client does not handle proxied DNS requests. All browsers end up going direct. Works find with the same server using an Android client.
Using a standard SOCKS Proxy, DNS requests are routed to the proxy server.
Just followed your guide to setup ShadowSocks on a Ubuntu 18.04 64bit VPS based in LA. Being a Linux noob, I had no idea what I was doing but your instructions were spot on. I am in China right now on a China Mobile sim and absolutely caning YouTube at 1080p!!! Long live Internet Freedom!
I just noticed Vultr removed their $3.50 sever. The cheapest choice now is the $5 sever. Could you confirm that @James ?
The $3.50 instances are still available but only on some locations. Right now it looks like there are some available for the New York location.
I’ve just setup a server in Alibaba Cloud (Starter Pack HK) and is working fine… 7USD/mo. I’ll keep using it until Wannaflix comes back…
Maybe this is already well documented, and my apologies if so. But for anyone just starting out with Shadowsocks, and most online guides referencing Vultr, I though it best to post this quick note.
Long story short, I email CS asking why no servers were working in China, and they confirmed that most if not all servers were not blocked inside China. Seriously, screw those guys. Would it be so hard to put a notice on the homepage or signup page?
But yeah, stay away from these guys. If you are building a Shadowsocks setup for China, absolutely no reason to consider Vultr.
This problem is not unique to Vultr. China is aggressively blocking ALL VPN and Shadowsocks servers this week. Things should be back to normal soon and most of the IPs will get unblocked.
I suggest trying a Vultr European location. I made one in UK during the last crackdown a few months ago and it’s still working toady. The GFW tends to block the USA servers more aggressively during the crackdowns.
Can any one suggest some vps that has good speed and support netflix?
I have heard about V2Ray and that it’s even more stable than SSR. Can you do a tutorial on that?
Thank you very much.I have been tried to setup a SS/SSR,but never worked.This article helped me.I am realy appreciate that.
Hey. Thanks James for your great post and detailed guide. Mine is working nice in Android.
I may change my Android phone to an iPhone. I just wondered if the SSR app for iOS has the split tunneling function (as I really need it and the function is available in the Android version of the app). Is there per-app proxy setting?
No, there is no per-app proxy setting for any of the iOS apps. I think this is a limitation of iOS because no VPN has split tunneling for iOS either. Shadowrocket has a setting called Global Routing that you can set to proxy or config mode. Config mode will bypass certain hosts according to a config file. I guess it’s similar to the Route=Bypass China setting on Android. But I heard that it doesn’t work very well.
@Sal
You can try Quantumult on iOS for split tunneling function
@Daniel
Thanks for your suggestion. However, I have tried all these 3 apps (Quantumult, Shadowracket, and Potatso Lite) and none of them works!!!!
It can connect to the server successfully, but I have no internet access after connection! (My phone is iPhone XS Max)
@James Do you have any suggestion? What should I do? 🙁
Hi,
How do you block local connections to shadowsocks?
This doesn’t seem to work on your one https://github.com/shadowsocks/shadowsocks/wiki/Block-Connection-to-localhost
I tried 5 IP from Seattle, all blocked. I’m pretty sure they are blocking every vultr IP right now. Usually I like to use this unconventional ISP (its an institutional one that is neither china telecom, china mobile or china unicom) cause the international bandwidth is pretty good compared to china mobile and china unicom. However it seems they are more restrictive during political events.
I’m just going to wait for the storm to pass and uses classic ISP for now. Thanks anyway, learned a lot here. Combined with haproxy, I feel like in my home country.
It’s not possible that all of Vultr IPs are blocked. My Seattle server is still working.
https://beta.speedtest.net/result/8314332182
Just keep trying, you will eventually get one that works.
I want to built more IP shadowsocks on one vps, how to do that? Thanks.
Hello,
I created several new instance on Vultr and I was unable to ssh to them since yesterday morning (I tried 5 different IP from different location).
I’ve got access to 3 ISP:
– on one of them, every IP was ssh-blocked.
– on an every IP worked (China Unicom)
– on the last it was pretty slow but worked (China mobile)
Anyone suffer the same issue? I’m afraid that every Vultr IP is blocked by the first ISP but it wasn’t the case before.
Many IPs are getting blocked because of the sensitive anniversary coming up in 2 days. My Los Angeles server was blocked the day before yesterday. I made a new one in Seattle and it’s working fine.
If you don’t want to deal with IP blocks, I recommend using the WannaFlix service, they are doing a good job of changing their server IPs when they get blocked.
Ok thank you for your quick reply. I hope it will pass, and will try again in some days.
I rather like vultr for now because of the access to a full vps which allows to do more things and I still got money inside x).
Try Seattle, mine is working good.
Hi there. Could you please tell me how to enable UDP for SSR? I added the line “mode”:tcp_and_udp to my ssr conf on the server but I didn’t help. I want to make calls on Telegram, but without UDP it cannot be possible.
Same experience with China Mobile here. On a second phone with Telecom SIM card, it works like a charm, while on my primary phone with China Mobile (which I sadly have to stick with) it doesn’t work in 9 times out of 10. Good to know that this is a common issue and it isn’t caused by some error on my part…
Thanks for replying! Unfortunately I am with China Mobile, too bad haha. Huge thank you again!
Thanks for writing a such in detail tutorial James! I’ve successfully set up my own SSR and I can not thank you enough! One question though, when I am using SSR on mobile data, it doesn’t work 99% of the time? It does get around 10 secs of connection after I turn on and off the airplane mode but doesn’t work right after. Huge thank you if you can help me out!
2 possibilities. If you are using Android, you need to disable “battery optimization” for the SSRR app. This will interfere with VPN and Shadowsocks apps. Another possibility is that you are using China Mobile. China Mobile can be very unstable with VPN and proxy connections, depending on your location (certain cell towers tend to be worse than others). China Unicom is much better.
Thanks for sharing this awesome blog post. I must say you have highlighted every bit of the information that is required to host shadowsocks server on vultr. While, I was wondering if the case remains the same with the managed vultr server which is powered by Cloudways. You can check for the server yourself by clicking on the below mentioned link: https://www.cloudways.com/en/vultr-hosting.php
I’m not familiar with Cloudways, but you should be able to do it if you have root access to the server. But I don’t know why you would want to when you can just get your own Vultr server for $3.50/mo.
As for Teddy Sun, he is done with his blog and will neither be working on any new scripts, nor updating the existing ones. The last post on his website from a couple of days ago is a goodbye message.
He probably removed the donation links even before that (payments through WeChat/Alipay can be traced) and did the same with tutorial articles (in Chinese) as well. He is leaving the master branch on GitHub open though, so the installation commands described in your article should still work – but the scripts won’t be updated in the future.
Apparently, SS/SSR has been successfully avoiding the “ever watchful eye of the people” for quite a long time, because it was probably too technical for the average user, but eventually it got too popular and therefore noticed. A number of Chinese developers involved got harassed by the wumaos and many of them ceased any further development as a result. One of those who persisted, known by the nickname of Toyo, was arrested last year, held at an unknown place for a few months and eventually officially prosecuted by the end of March 2019 with the “crime of providing tools for unauthorized access into computer systems”.
Hello James. I have one question, please help me if you know. I’m using Potatso Lite on IOS. Sometimes Potatso loose connection, and I restarting program, and it’s works. Some days , I have loose connections for 20 times of the day. What problem may be with my server configuration? Maybe I will change timeout parametr?
Don’t use Potatso Lite, it doesn’t work very well. Pay the $3 for Shadowrocket.
Hello, your post has been used as a technical source and a link back provided to your website from https://fanqiangdang.com/forum.php?mod=viewthread&tid=308
Hi.
*** China GFW is throttling speed (For all International connection) once it gets suspicious. ***
Recently I made a VPS exactly as you mentioned at Vultr (I don’t know how to thank you enough). It was fine. But I found D/L speed reduces at night. I played with the ports, cipher etc. then found even without ssr, my speed for international connections reduced to 0.5 ~ 1.0 Mbps. For everything. It continued for next 24 Hr. I went to next door of my apartment who uses the same package of China Telecom. His speed is normal (Around 30Mbps) for the same testing server. But I was getting full speed 98Mbps+ for inside China connection.
I though may be as VULTR doesn’t have CN2 connection, may be thats the reason. Afterwards I purchased another VPS package from Bandwagonhost. They have direct CN2 connection. No use. As my international connection speed is being actively throttled by GFW.
I went to my friends home. I tried to connect to my VPS with my friends connection. The speed was great. But within few hour, his speed was taken down to 1 Mbps. Even I left his home, his speed is still down for intl connections. Its a new Technique and BAD Sign.
Interesting behavior. Thanks for sharing. I haven’t noticed anything like this myself. Are you sure that your your ISP is China Telecom direct and not a China Telecom reseller ISP?
In any case, I think the international throttling is done on a local level. I suggest you try the WannaFlix service. They have a few “VIP” servers that will solve your problem. These servers are routed through domestic China servers before connecting to the endpoint server. That way you are only using domestic bandwidth, the international connection is made by the forwarding server in China. This is normally used by people with reseller ISPs that have poor international bandwidth.
You can also set this up yourself by renting a VPS in China and installing haproxy to forward the traffic to your SSR server. But it’s much easier and cheaper to just use WannaFlix.
@morris,@James Thank You so much for Your help!!! It works!!! You are genius!!!
Hello! I have done all thing You write. It’s realy works! I live in China and now I can use all blocked sites. But I have one problem, I could not download video from youtube. Maybe You have idea why? Usually I use SaveFrom, Download master and Internet download master.
The regular SS/SSR software only works in web browser,
If you want to use SS/SSR to download file(s) with downloader software (like IDM) or playing game, you can use this software to connect.
this software work on program (.exe)
https://www.sockscap64.com/sstap-enjoy-gaming-enjoy-sstap/
See the answer from morris. Or you can tunnel an OpenVPN connection over SS. Here is the guide:
https://www.tipsforchina.com/how-to-tunnel-expressvpn-over-shadowsocks-for-increased-speed-from-china.html
Thanks for your help. There’s somes questions with ss puzzled me. When I connect network at home , the ss works well. But when I’m doing this at company, it just broke down, don’t know what’s going on here. If you have some ideal about this, please give me some suggestion, thank you.
No idea. Maybe your server got blocked while you were at work.
Hello, James
Thank you James for the manual.
I have a little question:
{
“server”:”0.0.0.0″,
“server_ipv6″:”::”,
“port_password”: {
“443”: “password1”,
“443”: “password2”,
“443”: “password3”
},
“local_address”:”127.0.0.1″,
“local_port”:1080,
“timeout”:120,
“method”:”chacha20″,
“protocol”:”origin”,
“protocol_param”:””,
“obfs”:”http_simple_compatible”,
“obfs_param”:””,
“redirect”:””,
“dns_ipv6”:false,
“fast_open”:true,
“workers”:1
}
Can I use 1 port for 5 devices?
You can use the same port on as many devices as you want.
How do I limit 1 port to only use 2 devices at the same time ?
For example: a phone and a computer
Thanks ad
Not possible.
Hello James, thank you are lot for your manual. I have one question,that very important for me. Do you have some ideas,how I can limit user’s per one port of Shadowsocks. Because users can easily share with configurations via QR code. Thank you for your time
No, I don’t know any way to do that. I suggest that you can use this QR generator to quickly make a QR code for each user.
https://iiii.li/ss&ssr-qr-gen/ssr
Or you can just tell everyone to scan the same QR code and then manually change the port number after scanning.
Hey James, thank you so very much for your wonderful guide. I’ve no idea how to set up a private server before I read your post: not only is it a fool-proof, easy to execute and comprehensive guide, but also a great way for people to start off learning about SS. Not to say it really gave me a peace of mind knowing that I have access to all my favorite sites that I rely on like coffee after moving to China.
Just FYI in case others have the same issue with Vultr and Singapore servers. I’m in China. For some reason, the Singapore servers won’t connect after the full setup. I’ve run servers across LA, Seattle, NY, London, Paris, Silicon Valley, and Japan. LA is still the best one and only one I haven’t needed to touch. The others start timing out / inconsistent connections after a month or two, so I’ll destroy the servers and startup another instance. The only one that’s not been able to connect thus far has been Singapore. I just tried four times, went through setup with no issues, but when I try to utilize the servers on my Mac or iPhone, neither are able to get an internet connection…weird. Immediately setup a London server and no issues for now.
Same here, worked like a charm until recently. Can still access the server via SSH no problem, but SSR does not let me connect to any websites anymore. Already reinstalled, played with the parameters etc. but it just will not work.
Did something happen?
Hi! How about a Linux client? Which one do you recommend?
Best
Hello guys, I have a problem When I customize multiuser,and restart service, it’s not work, work only default port and password which i installed in first setup. What it can be?
This is my config file:
{"server":"0.0.0.0",
"server_ipv6":"::",
"port_password": {
"443": "di2la2n1",
"993": "111",
},
"local_address":"127.0.0.1",
"local_port":1080,
"timeout":120,
"method":"chacha20-ietf",
"protocol":"origin",
"protocol_param":"",
"obfs":"http_simple_compatible",
"obfs_param":"",
"redirect":"",
"dns_ipv6":false,
"fast_open":false,
"workers":1
}
I think you need to remove the comma at the end of the “993”:”111″ line. When you enter a list of items between the {} symbols, there is no comma after the last item.
It should look like this after you remove the comma.
"port_password": {"443": "di2la2n1",
"993": "111"
},
Thank you for your help.It’s works. It was my silly mistake.
Hello. I study in China. I followed your post exactly the way you showed us. And now I can search anything on Google and Youtube. But one thing. I can’t access Facebook. I don’t know why. What did I miss?
SS vs SSR, honestly, fully open sourced, maintained and documented shadowsocks-libev has never let me down. And in fact with plugin does support additional obfuscation, which seems to target ISP specific bandwidth throttling. SS (using AEAD cipher, wo obfs) is, in practice, undetectable, still, by GFW. And in my experience faster as well. V2Ray’s VMess may offer some real competition. SSR is obsolete / was never needed
I have to disagree with you that SSR is obsolete / was never needed. For me and many others in China, it is more stable and reliable. With SS, I often had to restart my modem after getting heavily throttled. I agree that SS has better English documentation and more active development. Actually, the development of SSR was stopped when the developer took everything off Github after receiving death threats from SS developers.
SS vs SSR is a very contentious issue with strong opinions on both sides. For me, I just use what works better, which is SSR. I will say that SS does have nicer clients though, and I wish someone would pick up the development of SSR and improve the Windows and Android clients.
I’ve heard V2Ray mentioned a few times but I don’t know much about it. What’s the main advantage over SS / SSR?
there are so many settings and factors to consider when getting throttled or blocked. There’s certainly no single SSR implementation and config profile. And just as many complain about throttles and blocks. I am saying when looking at the techniques employed they are mostly jargon and very little evidential difference or improvement. While it is great to learn you have a stable and performing overseas connection, this is undoubtedly possible with vanilla. Again I’ve been using SS (especially libev) for years accross multiple VPSes, locations, users, devices, ISPs, OSes, etc. Up to 60Mbps which is well beyond what’s needed for 4K streaming. Neither me nor my friends using my service ever complain.
V2Ray is a highly configurable tool supporting multiple protocols including Shadowsocks. Yet I think their own anti DPI protocol Vmess may proof useful or even superior in case SS throttling and blocking becomes evidential rather than anecdotal
thank very clear, Can you make a tutorial how to setup shadowsocks manager
Thank you.
Thank you James for your wonderful guide. I set up a ShadowsocksR server with the aim of playing in a french Minecraft server. (I already have Express vpn BTW but it is not enough). Chrome, Firefox and Edge work like a charm. Should I set Minecraft proxy https://imgur.com/cJSQVmd with 127.0.0.1 port 1080 or with my SSR Windows client settings ?
I’m not sure if Minecraft supports SOCKS5 proxy connections or not. Try entering 127.0.0.1 port 1080 with the password blank. If that doesn’t work, you can try connecting to your server using this
client instead of the standard one.
https://www.sockscap64.com/sstap-enjoy-gaming-enjoy-sstap/
It will force all connections to go through the proxy and has some settings specifically for gaming. Not sure exactly how it works, I don’t play games myself.
It works !!!!!
I first tried entering 127.0.0.1 port 1080 with the password blank. This doesn’t work. Then I downloaded the client from https://www.sockscap64.com/sstap-enjoy-gaming-enjoy-sstap/. I clicked on “add a SS/SSR proxy” and entered my proxy data.
And it work like a charm. You made my day.
Just a quick question: This client displays a number of “Connections” You can see it here https://imgur.com/N7pv5u9 at the bottom right. What is it ?
Moreover google says my connection “is not private”. Should I worry about something ?
I’m not sure what that means, maybe it’s the number of current TCP connections that are being made through the proxy. I’m not really familiar with that program. I just discovered it recently and
haven’t tested it much.
I’m not sure what you mean about Google saying your connection is not private. Maybe you are on a non-secure website (http instead of https)? In that case, it’s normal.
This works well for me. Setup a China internal server with Alibaba in there China data centre. VPN intitally to that, supper fast. Then setup a VPN from the Alibaba internal to Japan Alibaba data centre. I think it works so well as there is always a constantly connected server to server secure connection via a China trusted network, and I don’t tunnel all the way out to Japan. I can watch youtube for years like i am in the west 🙂
There is no need to do that unless your ISP is one of those re-sellers. If you get your internet directly from China Telecom, China Unicom, or China Mobile, then you just need an Alibaba CN2 location (Hong Kong or Singapore) to connect directly. Alibaba Tokyo is not CN2, so that’s why you need to route it through a domestic server to get good speed. Your Tokyo server can still get blocked this way too, so no real advantage unless your ISP is a re-seller (their international bandwidth is too much oversold even for a Hong Kong CN2).
Hi~ I followed your guide, and got a ssr server. I can access youtube.com now, but when I access https://google.com, chrome give me this error: NET::ERR_CERT_COMMON_NAME_INVALID. Do you have any ideas?
hey found something weird. after successfully accessing taobao with default config all of 2018, was unable to access it starting a week ago.
changed proxy rule from bypass LAN and China to bypass LAN. now able to access taobao again. i have no idea what the hell the problem was or why this settings change fixed it. thought i’d make a contribution and mention the solution here.
That is indeed very weird. Using the setting “bypass LAN & China” should bypass the proxy for Taobao and it should be the same as visiting Taobao without any VPN or proxy. I just tested this with my servers and I can load Taobao with either setting. It loads much faster with the bypass LAN & China option.
Have you tried different browsers or incognito mode? Maybe you got a bad cache file or cookie from Taobao that is causing this very strange behavior?
Does this still work, specifically on Mac/iPhone? I had my server working since earlier this year, but just returned to China after a couple months of travel and found that I could connect to my Vultr server using ShadowsocksX-NG-R8 on Macbook and PotatsoLite on iPhone, but that no websites would load. I even destroyed that server and followed all the instructions again with a new server but it still doesn’t work. I’m baffled since it worked so well for me on both devices before. Has something changed?
Yes, it still works. Your server IP might have been blocked and your new server’s IP could have already been blocked as well. If you can connect to your servers by SSH without a VPN, then it is not blocked. If you can’t connect by SSH without a VPN then it’s blocked. Try again with a new server and repeat the process until you get one that isn’t blocked.
I can’t seem to get obfs to work with shadowrocket on ios. On the server I have:
“obfs”:”http_simple_compatible”,
“obfs_param”:””,
And on the Shadowrocket client I have obfs set to http with no path or parameters.
If I turn off obfs, it works perfectly. Any ideas why?
That’s strange. I have no idea why it wouldn’t work for you. I have tested it on Shadowrocket with an iPad and everything works fine for me. Have you tried it with another client such as Windows or Mac to confirm if the problem is specific to Shadowrocket?
Thank you ! Really ! My personal VPN got banned from China so I lost all access to my mails. I can confirm that your optimization parameters gives me a 2x speed ratio.
You’re welcome. Glad that the optimization improved your speed.
Hey James, Thanks again for all the updates, it helps a ton! Have you found a way to “scramble” the IP, so that the Great Firewall doesn’t detect too much pattern on our Server IP? I am using the obfs parameter “cn.bing.com”, as I understand it helps make it look like you are accessing Bing all the time (I wonder who would do that in real life :/), but something for IP would be even better.
The GFW is not that simple, you can’t fool it so easily to think that all of your traffic is going to cn.bing.com. In my experience, it works best to leave the parameter blank. There is nothing you can do to prevent your server from getting blocked. Just be ready for it and make a new server when this happens.
Thanks for the instructions. Took some tinkering around, but finally got there. Seems the issue I had was the initial server isn’t working. Destroyed, tried again and worked. I cant get any of the UK ones working though.
My question is, If I want to run both Japan(current set up) in say a US server for shadowsocks, for SS app, do i need to repeat all the above steps? or just add the new server to the SS app?
many thanks
@Robby
You should be able to get a UK server that isn’t blocked if you keep trying. If you want to run 2 servers, you need to complete all the steps on both the server and client for each server.
I seem to keep getting stuck between these two steps:
I do not see net.ipv4.tcp_congestion_control = bbr anywhere 🙁
Also, I have no idea how to add anything to this file. Any help with this would be greatly appreciated – I have no idea what I am doing, but I’ve been trying to follow your instructions as explicitly as
possible, however I keep running into problems on this step.
After you type the command “nano /etc/sysctl.conf” then you should see the net.ipv4.tcp_congestion_control = bbr line at the bottom of this file. If it’s not there then your bbr installation was not successful.
hi guys is there a way to do this with a vps using hyperv virtualization? i’m shopping for a new option because vultr tokyo performs pretty badly for me here in xiamen. the kvm limitation is makes it tough to find other options.
I’m not sure but many providers are offering KVM virtualization, not only Vultr. If you are looking for the best speed, try Aliyun.
hello im very thank full with your article i did all the steps you said and everything is fine with my phone but when i enable it on my pc chrome cant open a web site with this proxy it cant load youtube pages but in my phone loads very quickly i live in iran and we do have restrictions as you
If it’s working in your phone then it should work on your computer too if your phone and computer are both connected to the same network. If not then you must have made a mistake when you entered the settings on your computer.
If it’s working in your phone then it should work on your computer too if your phone and computer are both connected to the same network. If not then you must havea made a mistake when you entered the settings on your computer.
Latest update, there are USD 2.5 instances available, but only with IPv6 support. Is it possible to still use the above method to setup a shadowsocks server?
Yes, I saw that Vultr is no longer offering IPv4 addresses with the $2.50 instances. I will update this page soon.
I don’t think there is any way to use Shadowsocks without an IPv4 address.
You can add an IPV4 address for an extra $2/month but you may as well just pay $0.50 more and get a $5 instance in a better location.
Any chance to use shawdowsocks behind proxy?
Hi James. Wanted to pass on my appreciation for a great tutorial. I had zero prior knowledge before attempting any of this. Thanks to you, I’ve got everything up an running. Life saver.
How to Limit the number of connections on a certain port? or to view active connections on a single port ?
Definitely a great guide. What about using only UDP for tunneling and passing all the traffic in a “VPN like style” on Windows? Games won’t connect at all, but simple http/s works like there is no tunnel. I suppose there should be a solution to this problem
My VPS has been working wonderful until now. Every website works except youtube, it doesn’t even load. What Might be the problem?
thanks alot man keep up the good work
@James
Looks like the most recent BBR causes a kernel panic with Ubuntu 14. I’ve used an older version and it works.
Just to let you know, every time I do the BBR steps on my ubuntu 16.04 at Kamatera, after rebooting the server is not reachable by SSH anymore.
Thanks for letting me know about the problems with the bbr installation. This page has now been updated with instructions on how to manually upgrade the kernel for bbr.
Hi bro. O like your working. So this doesnt work for me on Mexico whit Telcel. Can you giveme a hand please
Is there any way to Setup this in Raspberry Pi 3? I need that support for RPi. Thanks
Hello, James
how to install ss-panel, ss-manyuser?
Hi James, i’ve solve my problem and want to share it here.
For everyone that had problem when accessing Instagram, like get “Suspicious Login Attemp” when login or getting error when liking post, I suggest you to set up new server in another server provider.
I set up new server on DigitalFyre and everything works well.
*Note: I’m not recommend set up new server on Digital Ocean. I already try host my server there and then get more error when accessing another website like google and website with cloudflare protection (too many captcha verification).
It sounds like you had a bad IP address, which can happen on any VPS provider. It usually happens when the person using the IP before you was abusing Google/Instragram/etc. Probably scraping data with a bot.
You try making a new instance with Vultr, and that should solve your problem as well.
Some providers are worse than others for bad IP addresses. Generally, Vultr is pretty good. The worst is Aliyun.
Well, i already tried many times make new instance but the problem still coming 😀
i’m located in xiamen and i’ve set up a vps on vultr in tokyo and one on gigsgigs in hk. they both work very well although the vultr server is a lot farther away and the speed is 30% of the gigsgigs. i use the gigsgigs server almost 100% of the time except for the occasional day when it dies for a few hours.
recently, the gigsgigs server will load youtube pages lightning fast as always, but the videos won’t play intermittently. the page and comments load very fast, but the video refuses to play around 80% of the time. i’ve got a support ticket into gigsgigs to see if they can help.
recently i’m looking to add a 3rd server for redundancy and to see if i can get gigsgigs level performance as far as speed, but without the failure to play youtube videos.
it’s tough to find kvm as a lot of hosts only offer openvz. any chance you can make a new section of the guide detailing how to get set up on openvz? i tried a while ago with an openvz vps on gigsgigs, and once i reached a certain step in the tutorial, the installation wouldn’t work. i forgot which step it was, but it definitely wouldn’t work on openvz. i tried many times and ultimately had to trash the server and just start again with a kvm one.
just an update and fyi, my support experience with gigsgigs has been pretty bad. they offered no help with the youtube video playback problem and blamed my local network environment. oh well…
Sorry to hear about the trouble with your Gigsgigs server. I have never tried them, so I can’t comment on your problem with YouTube playback. Are using using Global Mode with Proxy Rule set to bypass LAN only or disable bypass? If not, try these settings. If that doesn’t work, try changing the DNS server on your VPS. It might be a DNS resolution problem when it tries to load the video. To change the DNS server on your VPS, edit the file /etc/resolv.conf and change the DNS IP to 8.8.8.8 and 8.8.4.4 (Google DNS). Then, restart shadowsocks. This won’t survive a reboot, so you will need make the change again if your server reboots for whatever reason.
Regarding OpenVZ, I think that everything in this tutorial should work, except for the Google BBR installation. If you can read Chinese, you can try this tutorial for installing BBR on OpenVZ.
https://blog.kuoruan.com/116.html
Hello James,
First of all thank you very much for this very detailed tutorial.
I have setup everythings as described on a raspberry pie on my home connection. It’s working perfectly for my US friend and myself.
But my Chinese friend can only access Chinese websites using it. Do you have any idea why ? Or maybe you know a way to debug why my friend can’t access most websites ? He is using Potatso for iOS.
Thanks again !
Hi James, thanks for sharing this tutorial, it’s really works for me. But, i have some issue when accessing social media like Instagram. When i accessing Instagram and like someone post, I always get error message “Action Blocked”. It always happen when i access it with Shadowsocks. I’ve tried change some setting in server like changing port, protocol, obsf, even deploy new server but this problem always happen. So, do you have any suggestion for solving this problem? Thanks
Are you having this problem on your mobile or computer? If mobile, then enable a setting in your client called “UDP Forwarding”.
I’m having this problem in mobile phone. I already try your suggestion but that error still happen.
Hey. First of all thanks for this insightful and detailed tutorial, it has been most helpful! I’m using the IPv6 configuration with shadowsocks, and am wondering: Does the Google BBR and server optimization also work with IPv6 packets? I keep reading net.ipv4…. etc., hence the question. If not, do you happen to know if there are some respective commands to optimize the server for IPv6 traffic?
Best, Jaffer
Sorry, no idea about that. I didn’t even know that it was possible to use SS with IPv6.
sysctl: cannot stat /proc/sys/net/ipv4/tcp_tw_recycle: No such file or directory how to do with this error?
I’ve never seen that error before. Are you following the tutorial exactly? Are you using Vultr or another provider? Which step is giving you that error? Need more information.
Hello @James,
Thanks a lot for your perfect article. i use it and now connect to VPN.
I have 2 questions from you :
1: how we can make limit each user can’t use this VPN for example more than 2 devices (make limit user connection).
2:How we can put limitation time for each user , for example one user cant use after one month ?
Thanks in advanced for your response.
Best Regards,
Kevin
Hello and great tuto,
Vultr setup works perfectly,
I have tried to copy this one for Alibaba Cloud but even if all seems just fine, using it from HK with a HK server is a big fail. I can’t connect at all, either with android or Windows, (when changing ip to vultr is working just fine)
Anything I should be aware if setting up one in Alibaba side? or it’s just not working?
Best
There are a few possibilities of why your AliCloud server is not working.
1. The IP address could already be blocked by GFW due to the person who used this IP before you. This happened to me once. I sent a support ticket and they changed the IP after I sent them a tracert and explaining that it was already blocked before I could even use it.
2. There is a setting called “Security Group Configuration” that you may need to configure. This is something like a built in firewall. You can find this setting on the main ECS page under the “More” option. Make sure that the necessary inbound and outbound ports are open. Or, open all ports as per below settings.
Authorization policy: Allow
Protocol Type: All
Port Range: -1/-1
Authorization Type: Address Field Access
Authorization Object: 0.0.0.0/0
Priority: 110
Same settings for both inbound and outbound.
Or, for better security, just open the ports that you need.
If you have the necessary ports open, see if your server will respond to a ping. If there is no response to the ping, try again with a VPN connected (if you have one). If the ping responds only with your VPN connected, then your server IP is blacklisted by GFW.
Hi James
I am using SSR and having difficulties to share my host VPN connection on VirtualBox VM. I am running Ubuntu 16.04 on VM but can’t access Google or FB while VPN is on in my host OS.
This the command i am trying to execute in Ubuntu terminal “curl -sSL https://goo.gl/6wtTN5 | bash -s 1.1.0-preview” but every time it returns connection failed message “curl: (7) failed to connect to port 443: timed out”. Someone said it happen due to proxy setting.
So it will be nice and helpful for me if you provide any solution for SSR.
Regards
Karim
What happens if you get caught using VPN/shadowsock in China?
Hi James,
Recently http_simple has become slightly identifiable. Try “tls1.2_ticket_auth” for obfs and auth_chain_a for protocol. For more info, check https://github.com/iMeiji/shadowsocks_install/wiki/ShadowsocksR-协议插件文档 and http://rt.cn2k.net/?p=328
really appreciate this resource James. i set up a server yesterday from my location here in xiamen on vultr tokyo exactly according to the instructions including the optimizations and the obfuscation. the connection worked very well for 24hrs. it was faster than lantern pro, 51chinavpn, and expressvpn. all of a sudden today my connection is completely non-functional on both my machines on which it was working well for 24hrs. all internet traffic fails completely including unblocked sites.
I don’t understand how my shadowsocks server on vultr could be identified and blocked by the gfw. how can this happen if the whole point of using shadowsocks is for avoiding detection?
I am also unable to connect to my vultr server using putty without activating a vpn such as 51chinavpn. and even when I connect to the vultr shadowsocks server using a vpn and restart it using the command
/etc/init.d/shadowsocks restart
and successfully seeing a message in putty that the application was restarted, activating ssr still results in total internet activity failure including connections to unblocked sites.
a Chinese friend let me borrow his company shadowsocks acct a while back and I tried connecting with it today after finding that my server no longer works. the connection my friend let me borrow still works. so it’s just my setup that won’t work anymore.
I have read in the comments here that the scenario I’ve described likely points to blockage by the gfw. however, I can’t understand how this kind of setup is a solution if it can be identified and blocked in only 1 day even with obfuscation set up as indicated in the instructions.
I’m terribly fearful of the February ban on vpns and am therefore trying to stay ahead of the problem by getting into place this kind of solution that cannot be defeated. I have reasons for needing to stay in china for a while and need real internet access as any western person living in this age does.
i was planning to set up 2 or 3 more servers in hk to have redundancies heading into February. but I can foresee serious problems and ultimate failure to stay ahead of the hounds if they can identify and block a server in only 1 day.
any help, guidance, or thoughts would be greatly appreciated.
“shadowsocks cannot be blocked by GFW” is a myth. The protocol may be more difficult to detect compared to VPN protocols but there are other ways to detect it. For example, by analyzing traffic patterns. if most of your traffic is going to the same IP address (your server IP) and there is no other normal traffic going to that server from within China then it can be assumed that it is some kind of VPN/Proxy. I’m not sure if this is how it works but it’s just an example I thought of.
As of now, shadowsocks server getting banned is still quite rare. The good thing about Vultr is that you don’t have to pay for time you don’t use and you can get another server up and running in 5 minutes. You can even backup your VPS and restore it on a new VPS if you don’t want to enter all the commands again. Be careful with VPS providers that require you to pay monthly and don’t allow you to change the IP address of your VPS.
Hey, thanks for the excellent tutorial. I’ve just got one question. I want to give out access to my friends but at the same time I’m afraid they might go on illegal sites. Is it possible for me to monitor what sites/ports (for example P2P ports) they might go on?
Thanks!!
Same answer as I gave to Cam. I believe those functions are available with ss-panel + ss manyuser. You could also try changing your firewall rules to block all the ports except for the SS server ports, port 80, and port 443. This would block torrenting for most users (unless they use one of the ports that is open).
Thanks for the tips! but I got a little problem with the google BBR. (OSX 10.11.6)
Everything goes fine until the last step of “Restart the shadowsocks server again.” with the command “/etc/init.d/shadowsocks restart”.
It shows: No such file or directory
Also, I got a question about the instruction below:
———————————–
Add the following line at the end of the file.
ulimit -n 51200
Finally, type the command below.
ulimit -n 51200
———————————————-
Do I need to input “ulimit -n 51200” twice?
Thank you for the help!
I’m not sure why bbr is not working for you, maybe OSX is not supported? Regarding the “ulimit -n 51200” command, adding it to the file will implement the setting every time your server boots. Entering it on the command line will implement it right away (but the setting will be lost after reboot without adding it in the file).
Is it possible to limit the number of devices per user/port?
I think it’s possible but that is beyond the scope of this tutorial and is also beyond the scope of my knowledge. If you are sharing your servers with many people, you should look into ss-panel and ss manyuser. As per my understanding, you can implement this and other features for multiple users more easily.
Thanks very much for this tut! Now I can switch between ExpressVpn and SS depending on the network speed/availability!
However for SS, I can’t access some (non browser based) apps on Windows (for example Netflix). How can I make it possible? Do I have to couple ExpressVpn+SS like explained in another tut?
SS only works with apps that have proxy settings or use the system proxy. For Netflix, it would likely still not work with SS, even if you could set proxy settings in the Netflix app. This is because Netflix is blocking all known commercial/data center IP addresses. You can confirm if your SS IP address is blocked by trying to watch Netflix in your browser instead of using the app. For Netflix, I would just use ExpressVPN. Either by itself or tunneled over your SS server following the other tutorial.
hi, i am just a simple guy I don’t have so much knowledge about internet. so I ask a simple question can I buy shadowsocks and where can I for a mac user
Send me an email, I can give you some suggestions.
Thank you so much for taking time to write this. Much appreciated.
I am currently using Astrill and it keeps dropping on me. Will hosting my own server like this fix this problem?
Thanks.
I can’t say for sure because I don’t know the reason that Astrill is dropping on you (it could be a problem with Astrill or it could be a problem with your internet connection). I haven’t used Astrill in over a year so I can’t really comment on how stable it is right now. I am using ExpressVPN, VPN.ac, and several shadowsocks servers. All of these are stable.
Hi James,
I found this article on the 9th of Oct, and everything worked out super smoothly. But recently, my connection keeps timing out. I was wondering if it was the encryption method? Maybe I should change it from chacha20 to aes-256-cfb? I’m not sure – could you give me your two cents?
[2017-11-10 11:36:35] System.Net.Sockets.SocketException (0x80004005):No connection could be made because the target machine actively refused it
at Shadowsocks.Util.Sockets.WrappedSocket.EndConnect(IAsyncResult asyncResult)
at Shadowsocks.Proxy.DirectConnect.EndConnectDest(IAsyncResult asyncResult)
at Shadowsocks.Controller.TCPHandler.ConnectCallback(IAsyncResult ar)
[2017-11-10 11:36:38] JOHNFRANK (45.XXXXXXXXXXX) timed out
[2017-11-10 11:36:38] JOHNFRANK (45.XXXXXXXXXXX) timed out
[2017-11-10 11:36:39] JOHNFRANK (45.XXXXXXXXXXX) timed out
[2017-11-10 11:36:39] JOHNFRANK (45.XXXXXXXXXXX) timed out
[2017-11-10 11:37:01] JOHNFRANK (45.XXXXXXXXXXX) timed out
Your server probably got blocked by the GFW. Just make a new one, and make sure that you are using SSR with obfs. The standard SS without obfs is not stable in China anymore.
Hmmm. The connection times out very often, but it still works every now and then. I will go ahead and deploy a new instance.
Just a side question as well – whenever I login with command prompt into the server – it says I’ve tried logging in several thousand times (the most I saw was 15000+ times) in the span of a week. Does this have to do with the connection timing out or is somebody/bot is trying to login/hack to the server?
Just wanna thank you in advance for the help and this guide. You saved my life dude!
It sounds like some person/bot is trying to brute force their way into your server. I would suggest changing the SSH port to another port and installing Fail2ban. Here are some links for further info.
https://www.liquidweb.com/kb/changing-the-ssh-port/
https://help.ubuntu.com/community/Fail2ban
https://github.com/shadowsocks/shadowsocks/wiki/Securing-Public-Shadowsocks-Server
Hey,
Thanks for the tutorial. There happens to be a lot more blocking and identification on the ss side recently, thought not the ssr side. Have you considered using V2Ray (https://www.v2ray.com/en/) at all? Would be awesome if you could write an article on it!
Yes, shadowsocks servers are getting blocked recently. I’m not sure if there is any difference between SS and SSR in terms of blocking, I think that is related to how much traffic your server is using.
SSR is much more stable. Without using the SSR obfuscation, I need to reboot my modem quite frequently.
I will look into V2Ray. It looks like a client that supports shadowsocks and other protocols? It’s not very clear whether it’s just a client or if there is something that you can install on your server that will use all of those protocols.
Thanks for the prompt response. I think the main differences among ss, ssr, and V2Ray are obfs algorithms. While ss does not do much obfs to avoid packet identification, the ssr tried to add the string
“http” in front of the packets after you select “http_simple_compatible” to avoid packet identification. We know that even ssr stopped development after July 2017, and it would probably become obsolete one day. My feeling is that V2Ray does the obfs one step further by having much more complicated obfs options such as “fake BT download”, so that it further decreases the chance of receiving resets, maybe even under greater data transmission speed. Unfortunately, I am not very adequate in programming/terminal commands. So I am just throwing it out there as something that you may find interesting. That’s being said, I don’t think V2Ray is updated frequently as well, and there may be other more advance things out there that are more advanced.
Here is an article in Chinese: https://oing9179.github.io/blog/2016/11/v2ray-More-Complex-and-Better-than-Shadowsocks/
THANK YOU SO MUCH
Hi,
When I deploy a server in Tokyo I can’t SSH to it without vpn. Is this normal? Should I destroy it and set up another one?
Yes, just start a new one. The IP has probably been blacklisted by the GFW.
Dude… Even if they trace the connection back to you with shadowsocks, they will not have any clue what’s going on because it’s highly encrypted, and the logs are stored on the VPS server and protected with a password that only YOU know. No need for the Hollywood style cyber scare show.
I’m not talking about the logs stored on your VPS. Rather, I’m referring to the risks of using a dedicated IP address that can be tied to your real identity.
“They” don’t need to see the logs on your VPS to know what you are doing online. Every website you visit or server you access can record your IP address and log your activity on THEIR server.
Using your own VPS does not give you the same level of anonymity and privacy as a commercial VPN service with a shared IP.
If you are only using your proxy to access YouTube, Facebook, etc and don’t care about privacy/anonymity, then it’s fine to just use shadowsocks by itself. You can do whatever you want. I’m just telling you what the difference is between a self-hosted server and a commercial VPN service and how you can use them both together if you want your online activities to be private and anonymous but still get the fast speed of shadowsocks.
Excellent!!! Thank you
Thanks, very useful.